1 - Getting Started #
The Australian Logic and Interstellar Exploration Network (ALIEN) needs your help! An unknown cyber actor has blackmailed ALIEN claiming that they will release their research unless they are paid a hefty sum. ALIEN believe that the information must have been stolen through a cyber intrusion, and have enlisted your help to work alongside the ACSC to investigate what has happened.
This part of the CTF is just about looking at the artefacts and data received, counting out the number of hosts and creating a checksum of a memory image. For this section I will use the following tools:
- FTK Imager
- PowerShell
- Volatility
- TrufflePig Nexus
GS-0 #
- Press submit on this one to continue.
GS-1 #
- Easy one, just count the number of zip files provided as they named by host.
GS-2 #
GS-2-1 PowerShell #
Because we are dealing with a RAW image file, we can use PowerShell to calculate the hash of the file itself.
Get-FileHash memory.raw -Algorithm MD5 | Format-List
GS-2-2 FTK Imager #
We cant always use PowerShell to get an image if there is compression or added metadata (such as an E01 or an AFF file).
- In FTK Imager, add
memory.rawas an evidence item.
- Click next and browse to where you have memory.raw decompressed. You’ll then have the memory image in the evidence tree section of FTK Imager.
- Right click on memory.raw and select “verify Drive/Image”
- Allow the verification process to complete, the results will be displayed on screen.
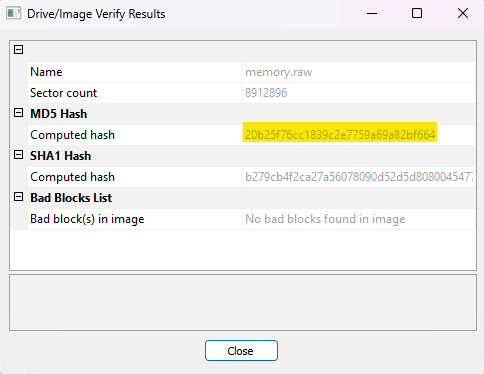
GS-3 #
I want to use a few different tools to get the answers and test out some new tools along the way, so I’ve started here.
GS-3-1 Volatility #
Installed Volatility3 in WSL2
Once Volatility was installed I ran the windows.info plugin to find the answer.
./vol -f "/mnt/c/temp/memory.raw" windows.info
layer_name 0 WindowsIntel32e
memory_layer 1 FileLayer
KdVersionBlock 0xf80732ea1f08
Major/Minor 15.17763
MachineType 34404
KeNumberProcessors 2
SystemTime 2021-04-06 01:56:57
NtSystemRoot C:\Windows
NtProductType NtProductServer
NtMajorVersion 10
NtMinorVersion 0
PE MajorOperatingSystemVersion 10
PE MinorOperatingSystemVersion 0
PE Machine 34404
PE TimeDateStamp Mon Nov 22 08:46:06 2010
GS-3-2 TrufflePig Nexus #
- Create a project in Nexus and import the memory.raw image.
- From the menu on the left choose “metaInfo”
- Scroll down to “SystemTime”
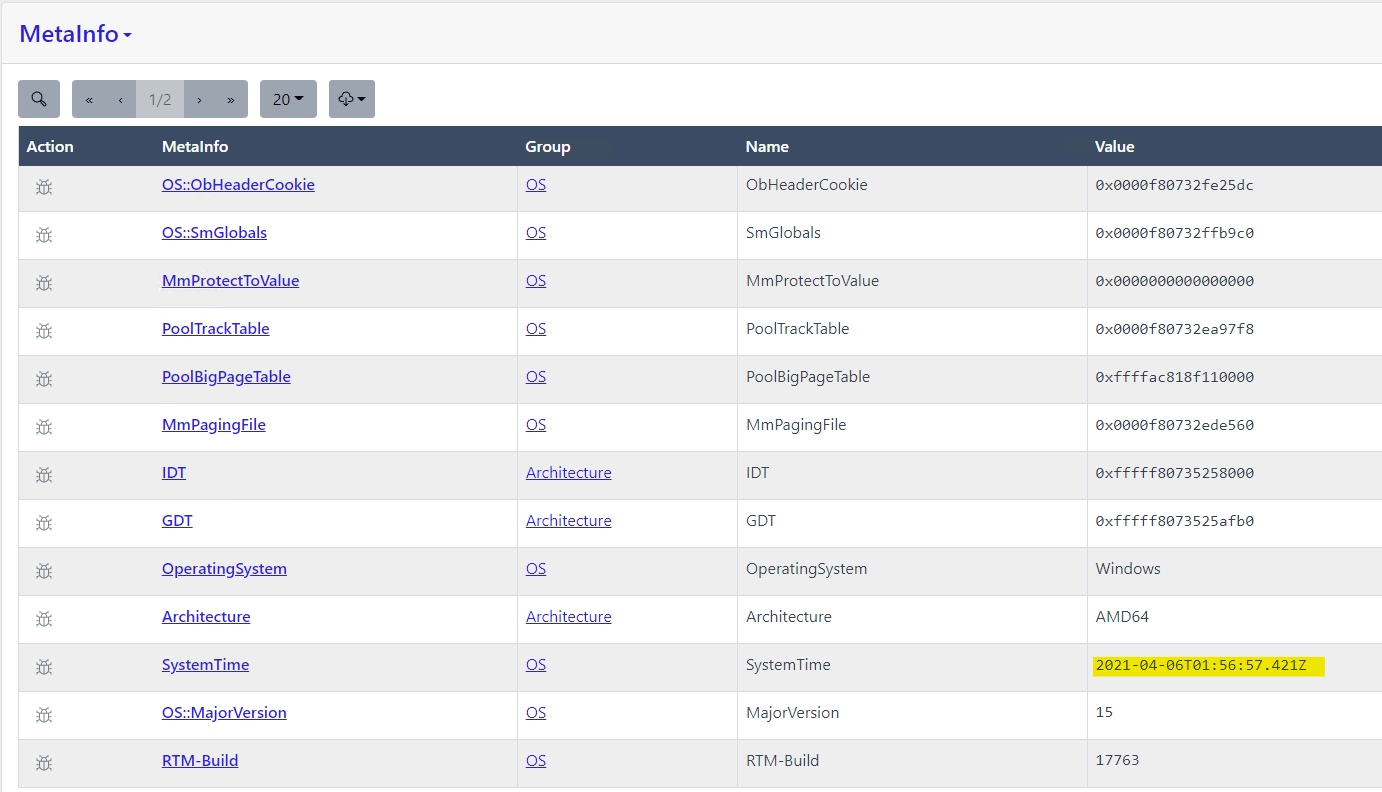
GS-4 #
- Just looked at the web log files and googled the cs_uri_stem
/Install/InstallWizard.aspx __VIEWSTATE=&culture=en-US&executeinstallto see what came back: