2.9 - RegRipper #
2.9.1 Lab Objectives #
By the end of this lab you should be able to:
- Use
gitto clone RegRipper to your Windows virtual machine. - Download RegRipper and run.
2.9.2 About RegRipper #
Harlan Carvey’s RegRipper, available at http://code.google.com/p/regripper/, is fantastic tool for getting data quickly out of the registry whether you are doing it for incident response or forensics. In essence what it does is produce reports based upon pre-canned registry searches. All you need to do is give it the registry file you want to review, give it a location for the report, and select the type of registry file. Then push a button.
RegRipper uses plugins to extract information out of the registry files. Each plugin has been created to handle the data that is stored in the registry key it has been setup to review. For example, the plugins will decode the ROT-13 encrypted data and translate binary data to ASCII.
RegRipper creates two files when it runs. The first is the report file that contains the output of the plugins that were ran against the registry file. The second file is a log file that contains the dates, times, plugins ran, and the number of errors that occurred with the plugins. The log file filename is based off of the report file name minus the extension.
2.9.3 Download RegRipper #
Open Terminal and from the command prompt type:
git clone https://github.com/keydet89/RegRipper3.0Then move into the RegRipper directory:
cd RegRipper3.0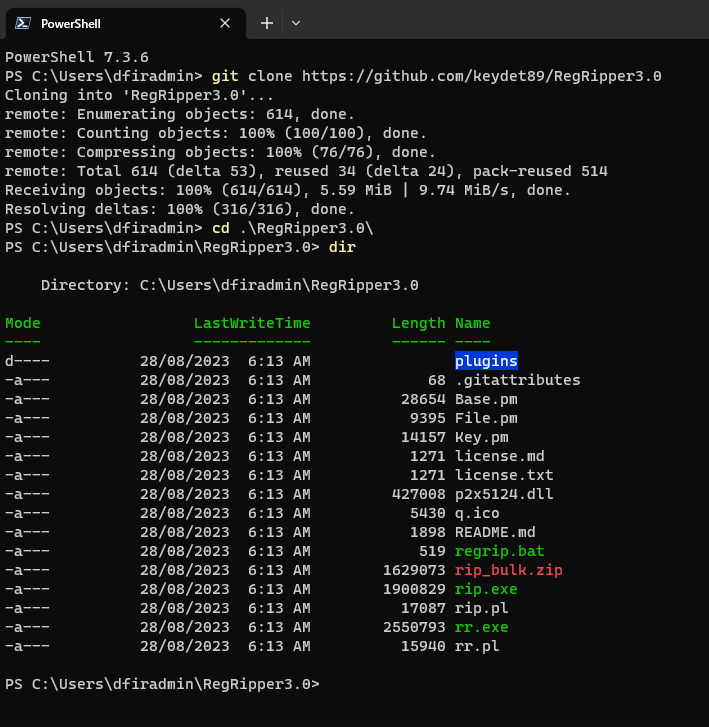
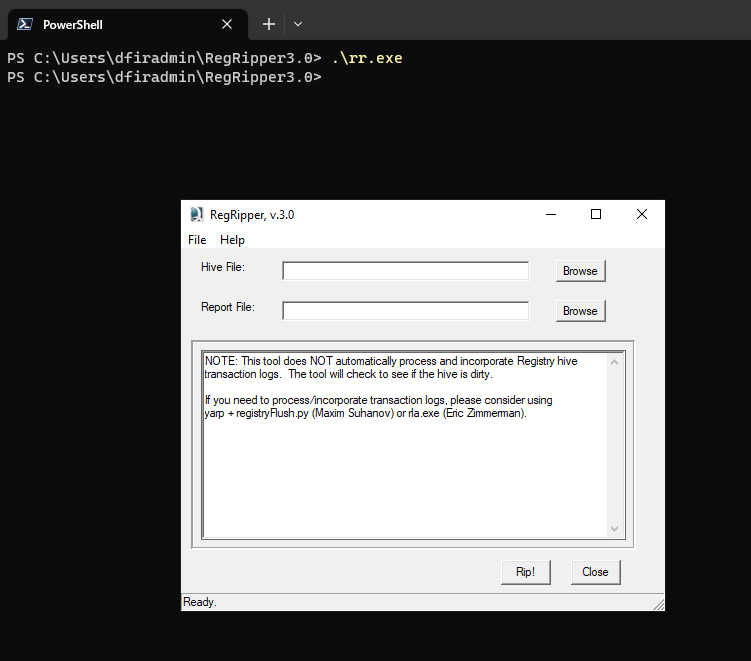
To run RegRipper GUI you can simply execute rr.exe:
.\rr.exe